Introduction
As the world becomes more complex, the U.S. Department of Defense (DoD) faces a range of challenges that demands innovative solutions. One tool that has proven invaluable in this regard is modeling and simulation (M&S)—the process of creating a representation of a system or process and then using that representation to explore and test different scenarios. The modeled system can range from a piece of equipment to an entire organization, and the representation can take many forms, including mathematical models, computer simulations, or physical mock-ups (Figure 1).

Figure 1. Example of a Soldier Using M&S (Source: Techviz.com [1]).
By using M&S, the DoD can explore scenarios and test concepts without risking personnel or equipment. In this article, we will explore the role of M&S in the DoD, its benefits, and some examples of its use.
M&S Used by the DoD
M&S used by the DoD is created by a range of organizations, including government agencies, defense contractors, and academic institutions [2]. These entities work together to develop M&S that meets the specific needs of the DoD. The DoD has several organizations dedicated to developing and using M&S, including the Defense Modeling and Simulation Coordination Office (DMSCO) and the Defense Advanced Research Projects Agency (DARPA). DMSCO is responsible for coordinating the use of M&S across the DoD, while DARPA focuses on developing advanced technologies that can be used in M&S applications [3].
Defense contractors are important players in developing M&S for the DoD. These companies often have specialized expertise in areas such as software development, systems engineering, and data analytics, all critical for M&S development.
Academic institutions also play an important role in M&S development. Many universities have research programs focused on M&S, and they work closely with the DoD to develop innovative technologies and techniques. The DoD often funds research projects at universities, providing resources and expertise to support M&S development. This involves collaborating between government agencies, defense contractors, and academic institutions, all working together to create effective tools that can support military planning and operations.
The DoD has a joint program to develop an integrated suite of modern computational engineering tools within an architecture that aligns both acquisition and operational business processes (Figure 2) [4]. The suite includes models, simulations, and related capabilities and trade space assessment and visualization tools. The U.S. Army is implementing a lifecycle approach for extensive and complex product data required in the engineering design, acquisition, and sustainment of military systems being adopted by the Army Combat Capabilities Development Command.
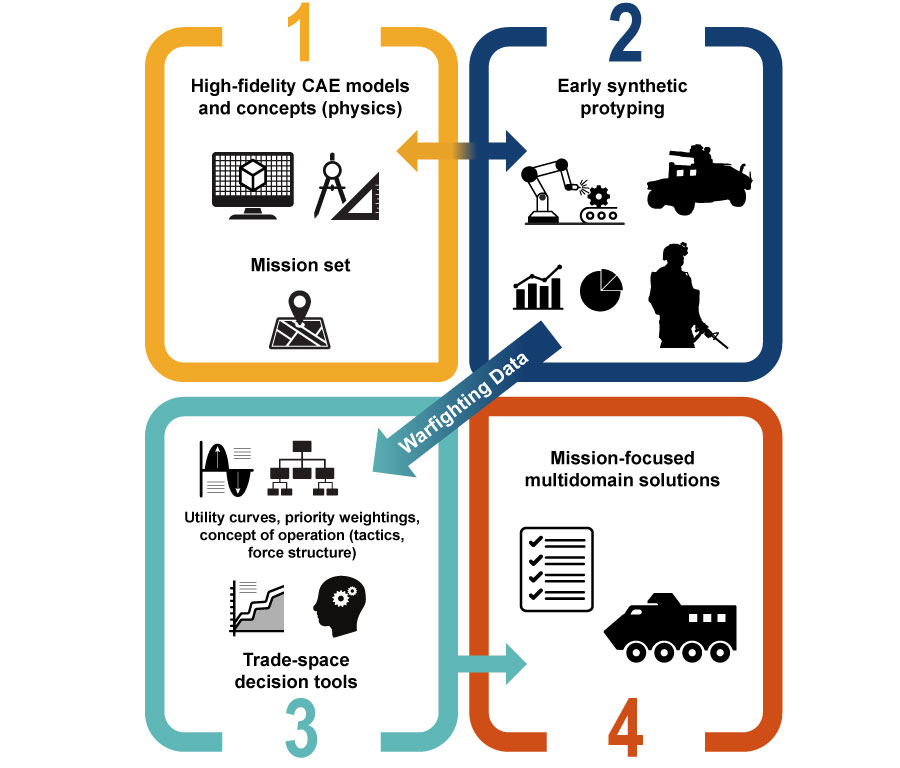
Figure 2. DoD Computational Engineering Tools Suite (Source: U.S. Department of the Army [4]).
The Benefits of M&S
The benefits of M&S are numerous—the most significant is the ability to explore scenarios and test concepts in a safe, controlled environment. By creating a model of a system or process, analysts can adjust parameters and inputs to see how the system or process reacts. An analyst might model the impact of a particular weapon on a particular target, adjusting variables like range, angle, and projectile type to see how the weapon performs under different conditions. This kind of testing can provide insights that would be difficult or impossible to obtain through live testing. M&S can also be used to explore scenarios that would be too risky, expensive, or time-consuming to test in the real world. For example, an analyst could model the impact of a cyberattack on a military network to see how the network would respond. This kind of testing, also known as chaos engineering (CE), can help identify vulnerabilities and inform the analyst of developing countermeasures.
CE is a discipline that aims to proactively uncover vulnerabilities and weaknesses in complex systems by intentionally injecting failures or disruptions. It involves running controlled experiments in production or testing environments to simulate various real-world failure scenarios and observe how the system responds. The core principle of CE is to expose and address weaknesses before they result in unplanned outages or service disruptions. By intentionally introducing failures, CE helps build resilience, identify potential points of failure, and improve the overall reliability and robustness of systems.
It is worth noting that CE should be conducted in a controlled and measured manner, with proper planning and consideration for the potential impact on users and business operations. It is not about inducing chaos indiscriminately but rather using well-defined experiments to gain insights and improve system reliability.
The economic benefits of M&S are just as impressive, including significantly accelerated time to market, drastically increased employment opportunities, whole-market growth, and innovative new products. This is only a glimpse of the potential impacts M&S can have. M&S can offer the following [5]:
- 98% reduction in prototyping and testing
- 25% reduction in safety incidents
- 55% improvement in energy efficiency
- 35% improvement in overall operating efficiency
- 55% reduction in water usage
- 30% reduction in consumer packaging
History of M&S and the DoD
The DoD has a long history of using M&S. In the 1990s, the Department embraced M&S to explore and test new concepts and technologies. One notable example is the development of the Joint Strike Fighter (JSF) [6]. The JSF program was initiated by the DoD to develop a next-generation, multirole combat aircraft that could replace a variety of existing aircraft across different branches of the U.S. military and be used by international partners.
The JSF program aimed to develop three variants of the aircraft—the conventional takeoff and landing variant for the U.S. Air Force, the carrier-based variant for the U.S. Navy, and the short takeoff and vertical landing variant for the U.S. Marine Corps and the United Kingdom’s Royal Navy.
The concept development phase for the JSF program began in 1993, followed by the System Development and Demonstration (SDD) phase in 2001 [6]. The SDD phase involved constructing and testing prototypes to validate the aircraft’s design and performance. The first prototype, known as the X-35, made its maiden flight in 2000. The following year, the X-35 was selected over its competitor, the Boeing X-32, to be the basis for JSF production.
Another example in the early 1990s is when The Boeing Company pioneered a new technique of designing a passenger jet entirely using computer M&S (Figure 3) [1]. Compared with traditional design methods used for the Boeing 757 and 767 designs, which involved physical mock-ups, the virtual design process resulted in the following design efficiencies:
- Elimination of >3,000 assembly interfaces
- 90% reduction in engineering change requests (6,000 to 600)
- 50% reduction in cycle time for engineering change request
- 90% reduction in material rework
- 50× improvement in assembly tolerances for fuselage

Figure 3. M&S Used by Boeing (Source: Techviz.com [1]).
Engineers utilized M&S to simulate the performance of the aircraft under various scenarios, enabling them to optimize the design and ensure it met the needs of multiple branches of the military and international partners [2].
As time progressed, the DoD expanded the use of M&S to support battlefield planning and decision-making [3]. Analysts also leveraged simulations to model different scenarios, allowing commanders to explore potential outcomes, evaluate strategies, and better prepare for contingencies. To continue future expansion of M&S, the DoD should focus on the following: technology advancements, interoperability, cloud-based solutions, synthetic training environments, scenario diversification, enhanced human-machine teaming, test and evaluation, and adaptive learning.
Recognizing the importance of human performance, the DoD also began utilizing M&S to optimize the capabilities of its personnel. Researchers employed simulations to study factors such as fatigue, stress, and decision-making under pressure. By modeling the impact of these factors, researchers could identify ways to improve training, equipment, and procedures, ultimately enhancing the performance of military personnel [7].
Logistics operations also benefited from the integration of M&S. With the vast scale of DoD operations, analysts used simulations to optimize the movement of personnel, equipment, and supplies. By modeling different scenarios and adjusting variables, such as transportation routes and inventory levels, they identified ways to improve efficiency and reduce costs [8]. In recent years, the increasing reliance on networked systems prompted the DoD to apply M&S to cybersecurity. Analysts simulated cyberattacks and assessed the response of networks, identifying vulnerabilities and developing effective countermeasures to enhance cybersecurity measures [9].
The DoD’s use of M&S has evolved into an integral component of defense operations. It has enabled informed decision-making, realistic training, optimized logistics, and strengthened cybersecurity measures. Looking ahead, the DoD will undoubtedly continue to leverage M&S, capitalizing on technological advancements to meet the evolving demands of the defense community [10].
Challenges
While the benefits of M&S are significant, there are also challenges to its effective use. One of the biggest of these is ensuring that models are accurate and represent the modeled system or process. Inaccurate models can lead to flawed insights and recommendations, potentially putting lives and resources at risk. To address this challenge, analysts must ensure that models are based on sound data and validated through testing and evaluation. Another challenge is ensuring that models are accessible and usable by a range of stakeholders. Simulations can be complex and technical, requiring specialized expertise to develop and use. To ensure that models are widely used and contribute to decision-making, they must be developed with the needs and perspectives of end-users in mind.
Finally, there is the challenge of integrating M&S with other decision-making tools and processes. M&S is just one tool in a broader toolkit for decision-making, and it must be used in concert with other tools and processes, such as data analysis and expert judgment. To ensure that M&S is effective, it must be integrated into broader decision-making processes and supported by leadership at all levels.
The Future of M&S
The future of M&S in the battlefield holds great potential for further advancements and applications. Increased realism is one of the potential developments that may shape the future of M&S. As computing power and technology continue to advance, M&S simulations will become more sophisticated and realistic. This will allow high-fidelity representations of complex systems, including advanced physics-based models, realistic terrain, and dynamic environments. The result will be more accurate simulations that provide realistic training experiences and improved analysis.
Artificial Intelligence (AI)
Integrating AI is another potential development in M&S. AI technologies can introduce intelligent agents and automated decision-making capabilities within simulations. AI algorithms can generate intelligent adversaries, simulate realistic human behaviors, and support autonomous decision-making, enhancing training, planning, and scenario generation [10].
Augmented Reality/Virtual Reality (AR/VR)
Integrating AR/VR technologies with M&S will offer immersive and interactive training experiences. Virtual environments can replicate real-world scenarios, allowing soldiers to train in realistic combat simulations, conduct mission rehearsals, and familiarize themselves with equipment. Augmented reality can provide real-time information overlays on the battlefield, enhancing situational awareness and decision-making. The advent and increasing use of haptics and touch will enhance immersion in AR/VR M&S applications. Haptics, which involves the sense of touch, plays a crucial role in creating a more realistic and immersive experience for users interacting with virtual environments.
By incorporating haptics feedback, AR/VR developers can add a sense of touch and physical presence to virtual objects and interactions. This technology allows users to feel textures, vibrations, and even the impact of virtual objects, making the experience more engaging and lifelike.
In AR/VR military M&S applications, haptics can have numerous practical benefits, such as the following:
- Training Realism: Haptics can make training simulations feel more authentic, enabling trainees to experience realistic, physical feedback in various scenarios.
- Skill Development: By providing tactile cues, haptics can assist users in developing and refining their skills in a controlled virtual environment.
- Immersive Gaming: In gaming applications, haptics can create a deeper sense of immersion, heightening the overall gaming experience.
- Medical and Healthcare Training: Haptics can be used in medical training simulations to provide students with a more realistic sense of touch when practicing procedures.
- Industrial and Manufacturing Simulation: Haptics can be applied in industrial settings to simulate interactions with machinery and equipment, aiding in training and safety.
The ongoing advancements in haptics technology, such as more sophisticated haptics feedback devices and better integration with AR/VR systems, have contributed to its increased adoption across various industries. As this technology continues to evolve, we can expect even more innovative uses of haptics to further enhance the immersion and effectiveness of AR/VR M&S applications.
Networked simulations will play a vital role in the future of M&S. With the increasing connectivity of military systems, integrating multiple simulations into a larger distributed network will enable collaboration, training, and joint operations virtually. This will facilitate realistic training for multinational forces, testing of interoperability, and evaluation of complex operational scenarios. Advancements in data analytics and machine-learning techniques will continue to benefit M&S.
By analyzing large datasets generated from simulations, analysts can gain valuable insights, identify patterns or trends, and inform decision-making. This supports optimizing strategies and developing new concepts and technologies. Real-time simulation and decision support will be crucial in dynamic situations. Linking simulations to real-time data feeds allows for rapid analysis and decision-making based on the evolving battlefield environment. This integration will provide commanders with the ability to evaluate potential courses of action and predict the outcomes of various tactical and strategic decisions.
Continued interdisciplinary collaboration between military organizations, academia, and industry will be essential for advancing M&S capabilities. Collaboration drives innovation, facilitates the exchange of knowledge and expertise, and fosters the development of innovative technologies. This ensures that M&S remains at the forefront of battlefield training, planning, and decision-making. It is important to note that these developments are speculative and depend on technological advancements, operational requirements, and the evolving nature of warfare. Nonetheless, M&S is expected to continue playing a vital role in training, readiness, and decision support for military forces in the near future [10].
Conclusions
M&S has become an indispensable tool, transforming the way military operations are conducted. The ability to simulate different scenarios and test concepts in a safe and controlled environment has revolutionized decision-making processes, reduced risks, and enabled the development of innovative technologies and strategies.
M&S plays a significant role in the advancement of defense capabilities, allowing analysts to explore a wide range of scenarios and optimize the performance of military systems.
While challenges exist, such as interoperability of simulation systems, data management, and the validation and verification of models, the benefits of M&S in defense applications are clear—it enables the exploration of new concepts and technologies, enhances training and readiness, optimizes logistics operations, and strengthens cybersecurity measures.
Looking to the future, M&S will continue to play a vital role in defense operations. Technological advancements will drive increased realism, integrating AI and AR/VR and enhancing the immersive and interactive nature of simulations. Networked simulations will facilitate multinational collaboration and interoperability testing, while advanced data analytics will provide valuable insights and support decision-making processes. Real-time simulation and decision support will empower commanders with timely and accurate information, enabling them to respond effectively to dynamic situations. The future of M&S in defense applications is bright, and its ongoing development and utilization will ensure the readiness and effectiveness of our armed forces for years to come [10].
References
- Techviz.com. “4 Use Cases for Virtual Reality in the Military and Defense Industry.” https://blog.techviz.net/4-use-cases-for-virtual-reality-in-the-military-and-defense-industry, accessed on 2 November 2022.
- U.S. Government Accountability Office. “Defense Acquisitions: Assessments of Selected Weapon Programs.” https://www.gao.gov/assets/320/315527.pdf, March 2011.
- DARPA. “Simulation-Based Design.” https://www.darpa.mil/work-with-us/simulation-based-design, accessed on 2 November 2022.
- U.S. Department of the Army. “Army Modeling and Simulation (M&S).” Army Science Board Fiscal Year 2020 Study, LinkClick.aspx (army.mil), 21 February 2021.
- National Training and Simulation Association. “A Primer on Modeling and Simulation.” https://www.ntsa.org/-/media/sites/ntsa/homepage/miscellaneous/ms-primer.ashx?la=en, 2011.
- JSF Program Office. “The Joint Strike Fighter: A Revolutionary Leap in Technology and Capability.” https://www.jsf.mil/downloads/docs/JSF_A_Revolutionary_Leap.pdf, 2003.
- Defense Science Board. “Assessment of Directed Energy Technology.” https://www.dsc.mil/ detechnology, accessed on 24 March 2009.
- U.S. Government Accountability Office. “Defense Modeling and Simulation: DoD Needs to Improve Its Management and Guidance to More Fully Leverage Capabilities.” https://www.gao.gov/products/GAO-19-64, 20 December 2018.
- Defense Logistics Agency. “DLA Energy: Modeling and Simulation.” https://www.dla.mil/Energy/Products/Modeling-and-Simulation/, accessed on 2 November 2022.
- U.S. Government Accountability Office. “Modeling and Simulation (M&S) in Defense Applications.” Defense Industry Information Analysis Center, https://www.dsiac.org/resources/white-paper/modeling-and-simulation-ms-defense-applications, April 2021.
Biography
Brian Nielson is the owner and chief executive officer of Kerns and Bellows Inc. (K+B), a company that specializes in content marketing, brand identity, and market research for defense and commercial companies and military organizations (including classified work) and analyzes data/uses digital media to create marketing and branding campaigns. His proficiency in artificial intelligence and 3-D design has allowed him to create interactive and responsive designs to meet the customers’ needs. He began his design and marketing career in broadcast TV in Manhattan, where he crafted visuals and graphics worldwide, and then transitioned into fashion. He also served in the U.S. Marine Corps as an MOS 8541 Scout Sniper, where he earned a triple expert rating for his shooting acumen. Mr. Nielson holds an associate degree from Campbell University and a BFA in graphic design and digital media from New York’s School of Visual Arts.


