Current methods for conducting cyber training are incompatible with the traditional, simulation-based training architectures used to conduct battlestaff training. As a result, there is little to no interaction between the cyber domain and the traditional warfighting domains during exercises.
This situation does not accurately reflect the current operational environment nor does it address the Secretary of Defense’s (SECDEF) and the Chairman of the Joint Chiefs of Staff’s (CJCS) directives and guidance for incorporating realistic cyberspace conditions into major Department of Defense (DoD) exercises.
The Cyber Operational Architecture Training System (COATS) is a U.S. Defense Modeling & Simulation Coordination Office (DMSCO) High-Level Task (HLT) that integrates existing cyber range environments, traditional simulation architectures, operational networks, and cyber emulations to safely and securely synchronize and deliver realistic cyber effects to the entire battlestaff – cyber for all. In doing so COATS provides an integrated and contested training environment where operators plan, execute and experience realistic cyberspace operations and conditions in all domains. This article describes the key components of the COATS architecture, including the application of network guards and the first draft of a cyber Data Exchange Model (DEM). This article also outlines lessons learned from the demonstration and employment of COATS during three U.S. Forces Korea exercises, U.S. Navy Fleet Synthetic Training (FST) events, and Operation Blended Warrior (OBW) at the annual Interservice/Industry Training, Simulation and Education Conference (I/ITSEC). Recommendations for future cyber and traditional modeling and simulation capability research, development, test and evaluation are also included.
Operational Problem
There is no controversy regarding the realities of cyber threats to U.S. interests at home and abroad. The DoD, in partnership with international, federal, state and local governments is tasked with defending those interests and enabling an open, secure and prosperous cyberspace environment for all. The April 2015 DoD Cyber Defense Strategy guides the development of cyber capabilities necessary to organize, train, and equip U.S. military forces in these missions. This guidance calls for the development of “… an individual and collective training capability … to conduct joint training (including exercises and mission rehearsals), experimentation, certification, as well as the assessment and development of cyber capabilities and tactics, techniques, and procedures for missions that cross boundaries and networks” (Carter, 2015).
The majority of today’s cyber training is conducted on dedicated, closed network “ranges” that provide the basic services and controls necessary to train DoD Cyber Mission Forces on their primary tasks and missions. While sufficient for this purpose, these ranges operate independently from the traditional M&S environments used to conduct battlestaff training across the spectrum of DoD operations, many of which are influenced by or rely on the cyber domain. As a result, there is a lack of integration with the cyber domain during major DoD exercises that limits the battlestaff’s ability to plan, integrate, and execute integrated cyber operations. Perhaps more importantly, this limitation restricts the battlestaff’s opportunities to experience and fight through degraded and denied conditions as required by the April 2014 CJCS Instruction 3500.01H entitled “Joint Training Policy for the Armed Forces of the United States” (Goldfein, 2014). Manual workarounds (e.g., “white cards”) can be used by exercise controllers to inject rudimentary degraded or denied conditions into exercises, but these workarounds are typically low fidelity and have little or no relation to the ongoing cyber war within the cyber ranges or the M&S environment used to stimulate the Command, Control, Communications, Computers and Information (C4I) systems in use by the battlestaff. Furthermore, white cards do not allow the training audience the opportunity to realistically detect, assess, and respond to a cyber attack. This situation is summarized in Figure 1 below.
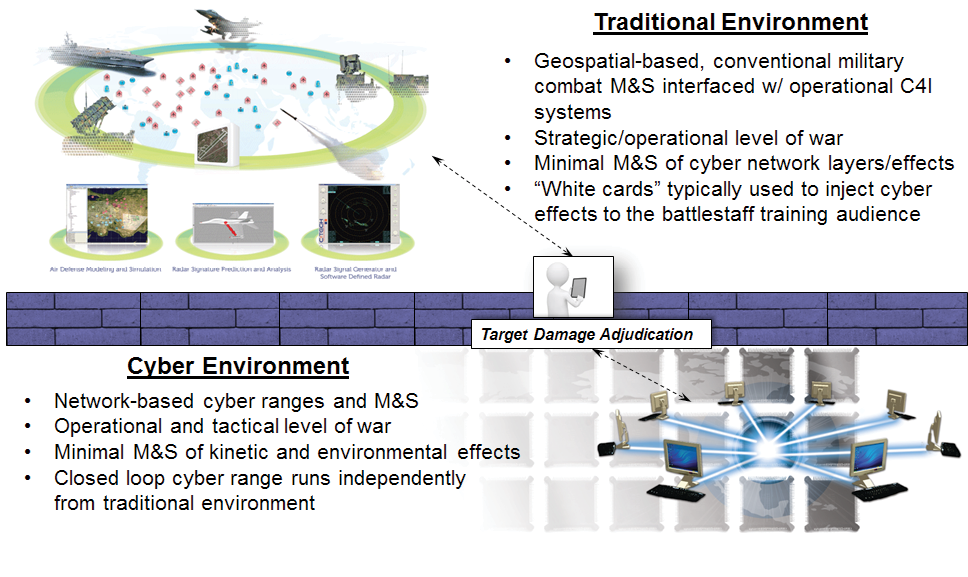
Figure 1. Current Exercise Environment – Source: Author
COATS Description
In 2014 DMSCO funded an HLT to develop an integrated training environment prototype capable of addressing the operational needs described above. COATS leverages and integrates existing cyber range environments, traditional battlestaff training architectures, operational networks, and cyber emulations to synchronize and deliver realistic cyber and traditional effects to the entire battlestaff. This integration is facilitated by the use of a network guard to protect and assure data flow between disparate networks and a new cyber Data Exchange Model (DEM) for interoperability between cyber and traditional M&S systems as depicted in Figure 2.
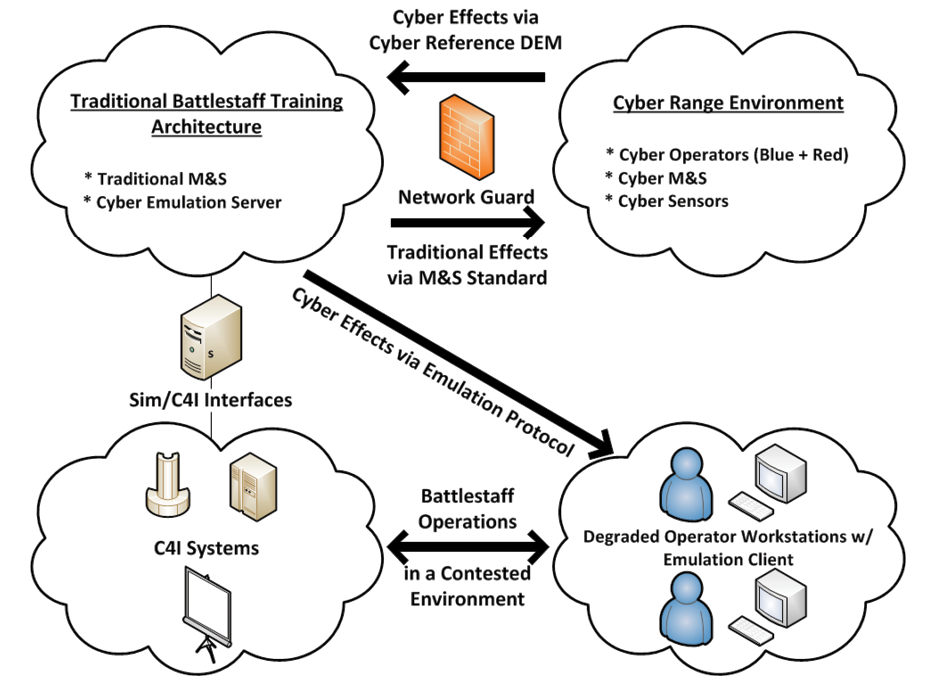
Figure 2. COATS High-Level Operational Concept Graphic – Source: Author
The critical components of the COATS architecture are the following:
- Cyber Range Environment – The cyber range environment is a collection of Live, Virtual and Constructive (LVC) cyber M&S tools and sensors used to create a realistic representation of critical networks, nodes, systems and message traffic correlated with the overall exercise scenario and forces. The cyber range environment is responsible for sensing cyber effects (not attacks) of interest, translating cyber effects into the cyber DEM, and passing over a protected network to the traditional battlestaff training architecture. Message traffic must pass through a network guard prior to receipt by the traditional battlestaff training architecture. A combination of open source, Government-Off-The-Shelf, Commercial-Off-The-Shelf and custom tools are used to create the cyber range environment such as Nagios, iperf, the Joint Network Simulation (JNETS) component of the USAF’s Air and Space Constructive Environment Information Operations Suite (ACE-IOS), and EXata. The cyber range is also responsible for receiving traditional effects of interest (e.g., kinetic and Electronic Warfare [EW] effects) from the traditional battlestaff training architecture and simulating those effects on the corresponding cyber range networks, nodes, systems and message traffic. Example effects include performance degradation, configuration changes and system failure.
- Cyber DEM – The cyber DEM is a draft standard developed by COATS partners that organizes and defines a series of data types that represent cyber effects of interest. The cyber DEM is necessary because there is no existing standard or method for sharing cyber M&S data within the DoD. Currently implemented as an eXtensible Markup Language (XML) schema, the cyber DEM can be easily applied to a DoD M&S standard such as the Distributed Interactive Simulation, High-Level Architecture, or the Test and Training Enabling Architecture (Morse, Drake, Wells, Bryan, 2014). The cyber DEM has been implemented as an XML schema in the U.S. Army’s Joint Land Component Constructive Training Capability (JLCCTC) federation and as a set of HLA objects and interactions in the U.S. Navy’s Navy Training Federation Object Model. The U.S. Air Force and the National Guard are both evaluating the cyber DEM as an extension to the DIS Information Operations Protocol Data Unit (PDU).
- Network Guard – An accredited network guard is required between the cyber range environment and the traditional battlestaff training architecture to assure and protect the applicable networks and systems. The network guard implements a restrictive ruleset that ensures that only approved messages, in the proper format, are securely passed from the expected sender to the expected receiver and vice versa. The network guard does not change or validate the classification level of the data. The U.S. Navy’s Radiant Mercury (RM) device, in tandem with the USAF’s ACE-IOS “Joint. Information Operations Range (JIOR) Broker” application, collectively acts as the network guard for COATS.
- Traditional Battlestaff Training Architecture – The traditional battlestaff training architecture is a collection of traditional (e.g., kinetic, EW, intelligence, etc.) M&S networks, protocols and software applications used to simulate key battlespace events and stimulate C4I systems and processes in use by the training audience. The USAF’s ACE-IOS system can detect traditional effects of interest (e.g., kinetic damage to a communications capability) and pass those effects to the cyber range environment through the network guard. The traditional battlestaff training architecture is also responsible for receiving and correlating cyber effects of interest (e.g., network performance degradation, system failure) from the cyber range environment and degrading the applicable simulated system capabilities and/or passing the effect to the cyber emulation to degrade the corresponding training audience network-based service or workstation.
- Cyber Emulation – The cyber emulation is an accredited tool for emulating network and host cyber effects on training audience workstations that have been sensed from within the cyber range environment. The cyber emulation does not affect the underlying network, nor does it damage the affected workstation. For COATS, the Network Effects Emulation System (NE2S) Master Control Station (MCS) is responsible for receiving cyber effects from the traditional battlestaff training architecture and initiating the corresponding emulated cyber effect on the applicable training audience workstation. Using a remotely-accessible web interface, the NE2S MCS provides situational awareness and positive command and control of emulated cyber effects. An NE2S client application is installed on each workstation to be affected that must establish and maintain secure communications with the NE2S MCS in order for effects to be initiated. Effects can be instantaneously started, stopped or adjusted from the MCS for an individual workstation, a group of workstations, or all workstations. If secure communications are not established or maintained, existing effects will timeout, no new effects will be initiated, and all affected workstations will be restored to previous (unaffected) conditions.
As depicted in Figure 2, COATS does not interface with or affect existing simulation-to-C4I interfaces used to stimulate the operational networks and systems in use by the training audience. COATS interfaces with M&S tools within simulation federations via the cyber DEM and affects operational workstations via the cyber emulation.
COATS USFK Deployment
The COATS architecture and associated technologies were deployed across the Continental U.S., Hawaii, and the Republic of Korea to support FY14/FY15 demonstration and training events with U.S. Forces Korea (USFK) and 7th Air Force (7 AF) during exercises Ulchi Freedom Guardian (UFG) 2014, Key Resolve 2015 and UFG 2015. The cyber range environment was provided by the USAF 90th Cyberspace Operations Squadron and used the Joint Information Operations Range (JIOR) and the network guard (RM plus ACE-IOS JIOR Broker) to share data over the Korea Battle Simulation Center (KBSC) Training and Exercise Network (KTEN) with ACE-IOS. ACE-IOS at the Korea Air Simulation Center (KASC) communicates with other M&S tools within the Joint Training Transformation Initiative + Korea (JTTI+K) federation (e.g., the Distributed Information Operations Constructive Environment) over KTEN as well as through a firewall to the NE2S MCS on the Combined Enterprise Regional Information Exchange System-Korea (CENTRIXS-K) network. The NE2S client software is deployed at USFK 7 AF to provide a contested training environment for the battlestaffs. A graphical depiction of this architecture is provided in Figure 3.
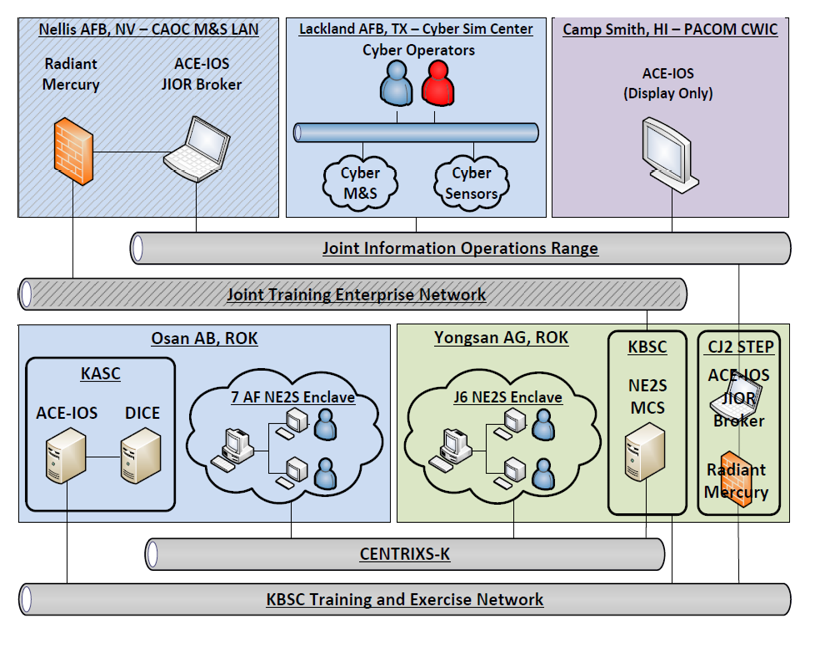
Figure 3. COATS USFK Deployment – Source: Author
The COATS USFK deployment supports four generic vignettes that can be tailored and integrated into the exercise scenario and Master Scenario Event List (MSEL) as required. The four vignettes are:
- Computer Network Attack (CNA) – Live red CNA against virtual blue systems to demonstrate virtual host degradation effects on live operator workstations. See Figure 4 for additional details.
- Physical Node Attack – Constructive red kinetic attack on a constructive blue communications facility to demonstrate C2 disruption effects on live operator workstations.
- Distributed Denial of Service – Live red CNA on virtual blue systems to demonstrate virtual full-motion video degradation effects on live operator workstations.
- Threat Network Degradation – Live blue CNA on virtual red networks to demonstrate constructive system degradation on constructive red systems.
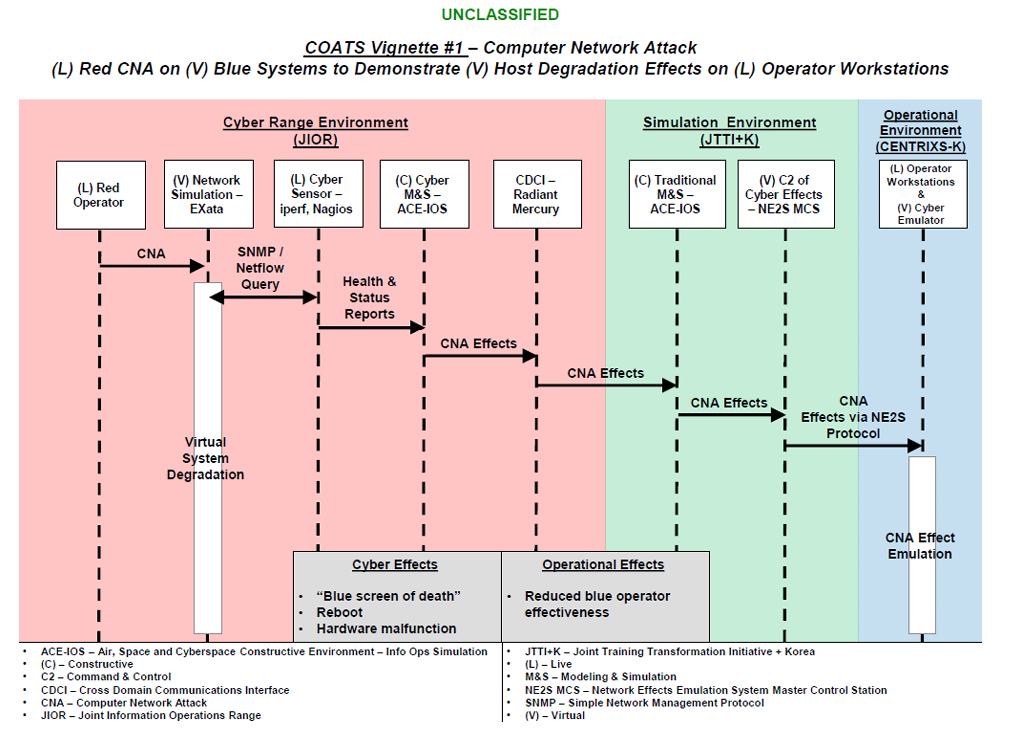
Figure 4. COATS CNA Vignette – Source: Author
COATS FST Deployment
In March of 2016, COATS was demonstrated during a Fleet Synthetic Training (FST) event sponsored by the Office of Naval Research (ONR). FST events are computer-assisted exercises conducted using models and simulations to stimulate and represent real world command and control systems. The Navy Continuous Training Environment (NCTE) supports FST by combining interoperable shore-based and ship-embedded systems into a single, distributed simulation network. In FST RDT&E 16-1, ONR and the CWIC collaborated to introduce cyber degraded training for the first time. Cyber attacks were executed and detected within a cyber range environment, transmitted to NCTE, and presented to the training audience in the form of degraded services. Using the cyber DEM and capabilities provided by mission partners, this proof-of-concept demonstrated one avenue for fulfilling SECDEF and CJCS direction to include realistic cyber degraded training in service exercises and training. Vignettes included:
- Compromised Common Operational Picture (COP) – A simulated coalition maritime patrol aircraft was targeted for physical compromise and malware was loaded onto simulated C2 systems. Once airborne in the demonstration scenario, data link track data was manipulated using messages based on the cyber DEM to degrade the COP and introduce doubt regarding position of hostile and neutral tracks.
- Degraded Full Motion Video (FMV) – A cyber attack within a portable cyber range environment targeted the FMV feed from a simulated Unmanned Aerial Vehicle (UAV) surveilling vessels of interest. Using the cyber DEM and NE2S, the display in the Coalition Maritime Operations Center was degraded, diminishing the ability to effectively identify and surveil shipping.
COATS I/ITSEC OBW Deployment
The COATS architecture and associated technologies were demonstrated at the 2015 and 2016 Interservice/Industry Training, Simulation and Education Conference (I/ITSEC). Operation Blended Warrior (OBW) was a cornerstone event of the conference integrating products and services of participants across the conference floor to demonstrate interoperability in a time-compressed demonstration. This LVC event was designed to represent a military exercise and demonstrate how integrated technologies can help commanders and exercise planners meet their training objectives. As lead for the cyber element of OBW, the CWIC introduced COATS to deliver cyber effects to the simulated Operations Center. Vignettes included:
- Degraded FMV – This vignette integrated a simulated UAV flying over simulated terrain with a cyber attack conducted within a cyber range environment. The attack was detected by COATS sensors, translated using the cyber DEM and sent to a workstation providing the FMV feed to the Distributed Training Center. NE2S installed on that workstation caused a simulated packet loss to the video feed rendering it unusable.
- Radio Frequency Attack on Satellite Uplink – Simulated transmission of interference of the FMV uplink to a simulated satellite was detected and translated into a cyber DEM-formatted message resulting in degradation similar to the network attack above.
- Degraded Voice Over Internet Protocol (VOIP) – Similar to the degraded FMV vignette, an attack in the cyber range, transmitted via COATS and cyber DEM, was interpreted by NE2S to simulate packet loss and render VOIP communications unusable until the attack was defeated.
- Insider Threat – Using a phishing feature in NE2S, a chat room interloper shared a link that resulted in degraded Operations Center workstations when selected by others in the chat room.
- Kinetic Effects Integration – As the finale of the degraded FMV vignette, the intelligence cell located the operating location of the cyber aggressors and a simulated tactical fighter aircraft kinetically destroyed the facility, restoring the FMV feed.
Lessons Learned
Key lessons learned from the planning, implementation, deployment and operation of COATS capabilities at USFK battlestaff exercises, service training exercises, and integration demonstrations are detailed in the following sections.
Planning
Planning for integrated cyber operations during a major exercise was the most significant and resource intensive challenge we experienced. Socialization and coordination of COATS activities was required across multiple organizations and throughout all levels of each organization (senior leader to action officer to technical support contractor). Past experiences with cyber training and exercises and a lack of understanding of the current state of the art often led to concerns about COATS and its potentially negative impact on the broader exercise objectives and training audience performance. As a result, an incremental approach was implemented that included multiple demonstration and test events to increase the battlestaff’s level of familiarity and comfort with the technologies. Once the technologies were verified and approved, the details and procedures for how to integrate and command and control degraded cyberspace conditions in a battlestaff exercise were immature or non-existent. Exercise planning products and exercise control procedures had to be updated to include measures and controls for implementing and monitoring degraded cyberspace conditions and had to be integrated and synchronized with the overall exercise objectives, scenario, and MSELs.
Reluctance to accept risk in implementing cyber events is not unique to traditional exercises. While the nature of technical demonstrations such as FST and OBW lowers the hurdles for introducing cyber warfare, the real or perceived risk means planners must be prepared to convincingly advocate for inclusion of meaningful cyber events. This may result in cyber vignettes conducted on the periphery of, or in parallel with, traditional or primary demonstration objectives. Ultimately, cyber planners should be prepared with an alternate plan to demonstrate cyber effects that traditional warfighters can relate to. Exposure of leaders to cyber is the goal; savvy leaders will grasp the ramifications of potential direct cyber effects and will help shape future events to emphasize cyber and prepare their staff and subordinates to fight through a cyber attack.
Implementation
The implementation of COATS at USFK required the integration of existing cyber range environments, cyber and traditional M&S tools, and cyber emulations across disparate cyber, training and operational networks. This integration required the development of the cyber DEM, modifications to existing traditional M&S tools to become “cyber aware,” and the use of the COATS network guard (RM and ACE-IOS JIOR Broker) to enable secure data flow between cyber ranges and simulation networks. Functionality and data flow were verified prior to each event as part of a Comprehensive Integration Test. The current implementation supports up to four generic vignettes that can be tailored and integrated into the overall exercise scenario and MSELs. Additional vignettes for different mission areas (e.g., Integrated Air and Missile Defense) are possible but would likely require additional modifications to traditional M&S tools to receive and realistically respond to the cyber effects represented within the cyber DEM. The risks and costs associated with the technical implementation of COATS at USFK were relatively low due to the reuse of existing capabilities and the straightforward integration strategy.
Deployment
The deployment of COATS technologies at USFK was most impacted by Information Assurance (IA) policies and procedures. Existing certification and accreditation products had to be reviewed or expanded before local authorities would approve installation and operation; approval via reciprocity was not an option. IA requirements for the simulation network (owned and administered by the KBSC) were different from those on the operational network (owned and administered by 8th Army’s 1st Signal Brigade).
In the FST and OBW demonstrations, the cyber DEM proved to be a flexible framework for conveying cyber effects. With little or no previous exposure to COATS, proficient developers were able to quickly adapt the model and expand on messages pre-scripted for NE2S. They developed cyber DEM messages to generate new cyber events including generation of nefarious link tracks and were able to generate effects simulating network packet loss. This is an important aspect of the overall COATS vision for an architecture and model that can mature to meet evolving requirements for cyber degraded training.
Operation
The operation of COATS technologies was straightforward and was aided by the personnel and associated roles and responsibilities detailed in Table 1.
Table 1. COATS Manning Plan – Source: Author
| Role | Responsibilities | Qualifications | Location |
|---|---|---|---|
| Cyber Subject Matter Expert (SME) |
|
Needs to be aware of COATS but does not need to be a COATS SME | Exercise control group / Cyber working group |
| Report results to the exercise control group |
|
Must be a COATS SME; must understand exercise control group Tactics, Techniques and Procedures (TTPs) | Exercise control group / Cyber working group |
| Report related issues to the COATS SME |
|
Must be a COATS technical SME | Various |
| NE2S Operator |
|
Should be a trained, trusted agent from the supported command | Anywhere on operational network |
| Report technical issues to the COATS technician |
|
Must be an ACE-IOS SME; could be an additional duty for an existing position | Simulation center |
Recommendations
The following recommendations are provided to assist current and future COATS sponsors, capability developers, users and maintainers with the successful development and employment of COATS and related capabilities.
Doctrine / Leadership / Policy
Joint Commanders must understand and direct their staffs to respond to existing SECDEF and CJCS requirements and guidance for incorporating realistic cyberspace conditions into exercises. “Military campaign plans must fully incorporate the ability to operate in a degraded cyber environment; military forces must exercise and be able to conduct military campaigns in a degraded cyber environment where access to networks and data is uncertain” (Carter 2015). “The Combatant Commands and Services should reduce restrictions that prevent testing and training against realistic cyber threats, and perform “fight-through” events to demonstrate that their critical missions are resilient in contested cyber environments” (Gilmore, 2016).
Leaders must understand and accept the risks associated with degraded/denied cyberspace conditions in exercises and encourage their peers and subordinates to incrementally improve the quality and quantity of cyber play. Accordingly, organizations should not be criticized for negative performance impacts as a result of conducting operations in a contested training environment. The SECDEF provides this guidance on the topic:
“During the Cold War, forces prepared to operate in an environment where access to communications could be interrupted by the adversary’s advanced capabilities, to include the potential use of an electromagnetic pulse that could disrupt satellite and other global communications capabilities. Commanders conducted periodic exercises that required their teams to operate without access to communications systems. Through years of practice and exercise, a culture of resilience took root in the military and units were ready and prepared to operate in contested environments.
Since the end of the Cold War, however, a younger generation has grown increasingly more accustomed to an environment of connectivity. The generation of military men and women that grew up since the end of the Cold War have had near constant access to information and communications, and the information revolution has led to a more agile and globally adaptive force. In the face of an escalating cyber threat, the lessons of the previous generations must now be passed down. The Defense Department must be able to carry out its missions to defend the country. Organizations must exercise and learn to operate without the tools that have become such a vital part of their daily lives and operations” (Carter 2015).
Training
Exercise program strategies, plans and products must be updated to increase the quality and quantity of cyber play in accordance with an organization’s concept and operational plans. Examples include exercise concepts, training objectives, scenarios, MSELs, exercise control group organization and procedures, and after action review/lessons learned procedures. An incremental approach is recommended to increase the leaders’ and the staff’s level of familiarity and comfort with any new technologies, processes and procedures. Consider conducting a small-scale table-top exercise or similar construct to practice key process and procedure changes prior to implementation.
Materiel
Additional materiel research, development, test and evaluation is necessary to expand and mature the current COATS technologies to better address the required mission areas and improve the level of interaction, resolution, and command and control of the integrated training environment as follows:
- Cyber Effects Resolution – The ability for cyber sensors, models and effects to interact with specific applications, services, ports and protocols.
- Virtual Network Generation – The ability to rapidly scan, generate, correlate and share network, system, and application deployment and configuration data between cyber ranges, traditional simulation architectures, and cyber emulators.
- Network Defender Training – The ability for network defenders to protect, detect, react and restore network operations based on feedback from and interaction with COATS sensors, models and effects.
- Threat Networks – The ability for COATS sensors, models and effects to realistically represent and degrade opposing force systems and networks.
- Cyber Range Command and Control – The ability to integrate and synchronize the management of cyber range environments with traditional simulation architectures (e.g., start/stop/pause/resume, checkpoint/restore, database synchronization, etc.).
- Cyber DEM – The ability to support additional mission sets (e.g., IAMD) and to be easily applied to existing DoD M&S standards.
Summary
This article introduced the COATS architecture and how it can be used to meet SECDEF and CJCS requirements for incorporating realistic cyberspace conditions into battlestaff training and exercises. The article also discusses lessons learned from the employment of COATS during three USFK exercises, two iterations of OBW at I/ITSEC 2015 and 2016, and a proof-of-concept demonstration of COATS integrated into a Navy FST event. Included are recommendations for future development and employment. Ideally COATS would be combined with other types of cyber training solutions (e.g., scenario injects and red teams) to provide a multi-resolution approach to integrated cyber training such as we see with the combination of LVC technologies used for traditional military operations training. It will take time for leaders and their staffs to become familiar and comfortable with cyber training capabilities such as COATS and it will take time for exercise programs to fully integrate cyber training objectives, processes and procedures into their existing products. COATS offers a near-term, verified method to synchronize and deliver realistic cyber effects to the entire battlestaff – cyber for all.
Acknowledgements
USPACOM would like to thank the following COATS sponsors, performers, and supporters for their dedication and expertise:
- Office of the Undersecretary of Defense, Acquisition, Technology and Logistics – Dr. Steven King and staff
- DMSCO – Mr. Jesse Citizen and staff
- Office of the Director, Operational Test and Evaluation
- Joint Staff J7
- USFK KBSC, Joint Cyber Center, J635
- 7 AF KASC, A3, A6, 607th Air and Space Operations Center
- USAF 90th Cyberspace Operation Squadron
- USAF 453rd Electronic Warfare Squadron
- Naval Air Warfare Center Training Systems Division
- Johns Hopkins University Applied Physics Laboratory
References
- Carter, A. (2015). The DoD Cyber Strategy. Page 17.
- Gilmore, M. (2016). Director, Operational Test and Evaluation FY 2016 Annual Report. Page 444 (Cybersecurity)
- Goldfein, D., (2014). CJCSI 3500.01H Joint Training Policy for the Armed Forces of the United States. Page D-7.
- Morse, K., & Drake, D., Wells, D., Bryan, D. (2014). Realizing the Cyber Operational Architecture Training
- System (COATS) Through Standards. 2014 Fall Simulation Interoperability Workshop. Page 7.


