Cyber-Physical Systems (CPS) and Internet of Things (IoT) devices such as sensors, wearable devices, robots, drones, and autonomous vehicles facilitate the Intelligence, Surveillance and Reconnaissance to Command and Control and battlefield services. However, the extensive use of information and communication technologies in such systems makes them vulnerable to cyber-attacks in the battlefield. These IoT devices are most often designed without considering security. Unprotected IoT devices can be used as “stepping stones” by attackers to launch more sophisticated attacks such as advanced persistent threats (APTs). An APT is a cyber-attack in which a malicious adversary gains access to a network and remains undetected for a long period of time. A later stage of APT is the “lateral movement” stage, where attackers use benign computer features to move step-by-step deeper into the network in a stealthy manner. For instance, it has been reported that Samsung’s smart fridge could be used to steal a user Gmail login. One can imagine several additional steps such as sending phishing emails to friend or coworker followed by privilege escalation. The above challenges and the high risk and consequence of IoT attacks in the battlefield drive the need to accelerate basic research on IoT security.
We are investigating proactive defense of IoT networks including cyber deception, cyber resilience, cyber agility – this process is also called Moving Target Defense (MTD). We consider the most intelligent adversaries that are able to launch sophisticated attacks (e.g. APTs). We also look into the scientific foundation of cyber security. Theoretical constructs and mathematical abstractions provide a rigorous scientific basis for cyber security because they allow for reasoning quantitatively about cyberattacks. In particular, game theory provides a rich mathematical tool to analyze conflicts within strategic interactions and thereby gain a deeper understanding of cyber security issues. By definition, game theory is “the study of mathematical models of conflict and cooperation between intelligent rational decision-makers”. The level of sophistication of recent cyber-attacks justifies our assumption of attackers’ rationality and thus the need for an intelligent defense mechanism based on game theory.
Advanced Persistent Threat
The cyber kill chain in Figure 1 shows the stages of an APT (red) as well as the defender’s best response at each stage (blue). At the reconnaissance phase, the attacker scans the system to identify potential vulnerabilities, understand the network topology, and find critical targets. This is followed by an exploit of a vulnerability to command & control a node. From that node, the attacker proceeds to a privilege escalation to gain elevated access that will enable lateral movement to reach a critical target. A proactive defense mechanism includes all scheme the defender can implement to protect the network before a cyber-attack is launched or early in the reconnaissance phase. Intrusion prevention systems (IPS), including firewalls and anti-virus, are designed to protect networks against cyber-attack attempts. However, these cyber systems tend to have inadequate prediction performance and misidentify malicious network traffic (e.g., malware, botnet) as benign—these packets are called false negatives. In addition to IPS, research shows that statistical learning techniques can accurately forecast or predict the timing and frequency [31] of cyber-attacks, based on network and organizational observations (e.g., domain name system traffic, network security policy). When proactive defense fail, the defender tries to detect the intruder, deny or disrupt malicious action or at least contain the attack. In the worst case of a successful attack, the defender should be prepared to quickly recover. The use of IoT devices in the battlefield increase the attack surface that our adversary can exploit. A game theoretic approach is suitable for all stage of an APT, from proactive cyber defense, to fighting through an attack in progress [9], or survive and recover from a successful attack [10]. Our prior work [9] uses stochastic game approach to contain a CPS attack in the lateral movement phase.
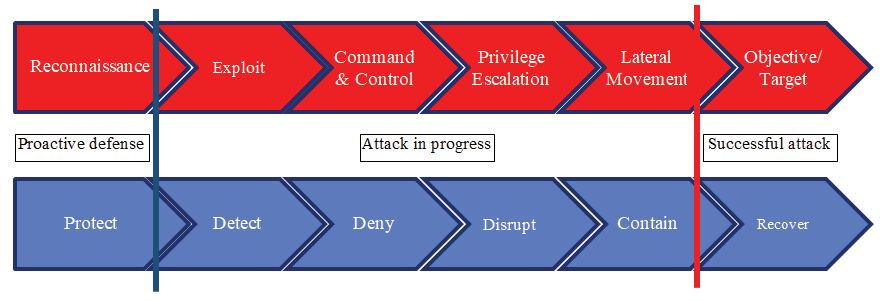
Figure 1: Cyber Kill Chain. (Source Author)
Proactive Cyber Defense
There are several challenges associated with IoT security compared to securing traditional information technology (IT) systems. First, IoT devices are rapidly mass produced to be low-cost commodity items without security protection in their original design. Even if a device initially has some security features, many IoT manufacturers do not provide any security updates and thus IoT devices can become unsecure as hackers discover new vulnerabilities. Second, IoT devices are highly dynamic, mobile, heterogeneous and lack common standards. Additionally, they have a limited battery capacity, memory, and processing power and cannot integrate standard encryption algorithms and security protocols. Third, it is imperative to understand the natural world, the physical process(es) under IoT control, and how these real-world processes can be compromised before to recommend any relevant security counter measure. When faced with these challenges to IoT security, a proactive approach is better suited to the defense of IoT assets. A proactive IoT defense allows us to plan in advance, analyze all cyber threats and gain a precise understanding of potential vulnerabilities before a cyber-attack is launched. Cyber deception, cyber agility [ also referred to as Moving Target Defense (MTD) in the literature], and cyber resilience are the main components of a proactive cyber defense. Those components can be used separately or in conjunction to protect IoT.
Cyber deception is any attempt to disguise a network and impair the attacker’s decision with false information to protect critical nodes. Deception can delay a cyber-attack by increasing uncertainty. Deception also forces the attacker to perform more trial and error in the reconnaissance phase which increases the probability of intruder detection. The use of honeypots is a basic form of cyber deception used to create the appearance of important targets to the attacker. Honeypots also help to identify attackers and provide a means to learn about their behaviors in a safe environment. The attacker’s strategies learned via the use of honeypots aid in securing critical components [11]. A honeynet is a decoy network that contains one or more honeypots. Valuable deception techniques must confuse the attacker while being transparent to the defender and legitimate users [12]. Advanced deception techniques can dynamically hide or create fake vulnerabilities, data, protocols, communication links, software and applications. However, given enough time, an attacker may be able to discover the defender’s deception strategy. Therefore, a sophisticated cyber deception technique is most often combined with cyber agility.
Cyber agility is the dynamic reconfiguration of network parameters, components, topology, and protocols to oppose an attacker’s ability to collect information about the system. A static configuration gives enough time to attackers to learn about the system and identify potential vulnerabilities or exploits in the reconnaissance phase. An agility strategy randomly changes the network pattern faster than an attacker can learn. The Army Research Laboratory’s Cyber Security Collaborative Research Alliance is currently investigating game theoretic approaches to cyber agility [13].
Cyber resilience refers to the network capability to continuously maintain mission essential functions after a cyber-attack. Resiliency must be an important consideration in IoT design for a number of reasons. First, the military uses commercial off-the-shelf (COTS) IoT devices available to the general public. Second, IoT devices interconnect with the commercial network not owned by the military. Third, most IoT devices are designed without concern for security and thus contain many vulnerabilities that can be exploited as weak links to gain access to more important targets. Fourth, it is beyond the capability of a developer or a network administrator to predict all natural failure and malicious attacks because of the increased interconnection, interdependency, and complexity of IoT networks. Those facts dictate our pessimistic view that some attacks may be successful regardless of efforts to maintain best practices in the areas of deception and agility. We should proactively design IoT networks while considering remediation against the worst case scenario, that of a successful attack. Resilient mechanisms sometimes involve system replication, to add redundancy and avoid a single point of failure [14]. Furthermore, the replica can be diversified to counter the attacker’s ability to exploit the same vulnerability in all replicas.
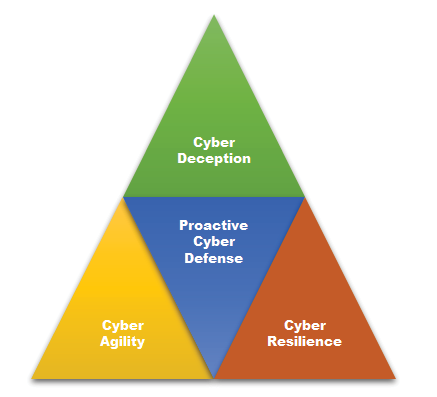
Figure 2: Proactive cyber defense. (Source Author)
Game Theory for Advanced Persistent Threat
A game in normal form is given by a set of players, the set of strategies available to each player, and a payoff function that allocates an award to each player given any combination of strategies representing the choice made by each player. Game theory is suited for proactive cyber defense because of its predictive power. The solution to a cyber security game is its Nash equilibrium (or its derivative). At a Nash equilibrium profile, no player can increase his payoff after a unilateral deviation. Also, each player is playing his best response to other players’ strategies. Therefore, the defender can use the Nash equilibrium profile to predict the attacker’s best action. The prediction power of game theory, combined with cyber deception, cyber agility, and cyber resilience can form the basis of a robust framework for proactive cyber defense.
Each player in a game attempts to maximize his payoff based on his information and his belief about others players’ information. If the set of players, strategies and payoff function is common knowledge, we have a game of complete information. Otherwise, we have an incomplete information game. Therefore, cyber deception and agility which interfere with the attacker’s ability to gain accurate information produces a game of incomplete information with the potential to diminish the attacker’s payoff. However, one must also carefully consider skillful attackers able to deceive the defender. A skillful attacker can behave as if the defender’s deception is effective to misguide the defender to reveal his mode of operation. A useful game model must consider several other possibilities that relate to incomplete information. A skillful attacker may develop unknown exploits (e.g., zero-day vulnerabilities), hide his true intent (i.e., target, payoff), or operate undetected for a long time —this is the intent of an APT).
Recently, there has been increased interest in the literature to apply game theory to cyber deception [15], [16] agility [17] resilience [10], [14] intrusion detection [18] lateral movement [9] and APT [19]. Cuong et al. [20] provide a detailed survey of these game-theoretic applications to cybersecurity. However, those works are restricted to a single stage of the kill chain and do not consider specific constraints of military IoT. We are currently investigating end-to-end defense mechanisms that can deal with a cyber-attack at multiple stages. The goal is to design mission-aware IoT with an autonomous cyber response capability.
We present a high-level description of our current approach to build an autonomous response [21] to IoT security with deception capability, learning for detection, and containing lateral movement. Figure 3 shows the diagram of the engine. From the configuration files of hosts (e.g., computers, operating systems, application, firewalls, servers, routers), the engine can compute the topology of the IoT network and generate the attack-graph. Two nodes V1 and V2 are connected in the attack-graph if there is a port, a protocol, and a vulnerable application on V2 that can be exploited to compromise V2 from V1. The engine incorporates a scanning tool capable of discovering new vulnerabilities from public vulnerabilities databases such as National Vulnerability Database (NVD) [22]. Once a new vulnerability is detected, the attack-graph is updated by adding new edges to the graph. We use the Common Vulnerability Scoring System (CVSS) [23] to compute a relevant assessment on how the attacker can access a vulnerability, how complex it is to exploit the vulnerability, and the number of times one must to authenticate (if any) in order to exploit the vulnerability. If a new patch is released from NVD, then the system will automatically apply the patch and updates the attack-graph by removing all the edges corresponding to the patched vulnerability.
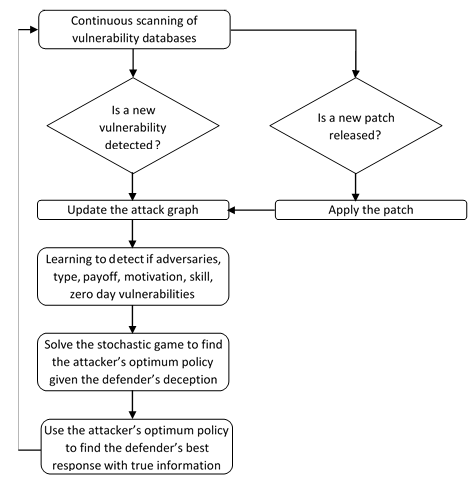
Figure 3: Best response engine for self-secured systems. (Source Author)
Before an attack is detected, a dynamic cyber deception mechanism is implemented to mislead the attacker and minimize the attacker’s impact on the IoT network. An adversarial machine learning approach robust to intelligent manipulation is implemented to detect these characteristics about the attacker: payoff, motivation, skill, and potential zero-day vulnerabilities not in the NVD database. The learning algorithm has to quickly converge to be compatible with fast changes in network topologies.
When an attacker is detected, a two-player stochastic game representing the interactions between the attacker and the defender is initiated. In this game, the states represent the nodes of the attack-graph and transitions correspond to the edge-vulnerabilities that the attacker can exploit to move laterally. The solution of the game will give the attacker’s optimal policy with deception.
Given the attacker’s optimum policy, the defender’s best response is calculated with accurate information. The best response at any state of the game will allow the system to quickly recover to a secure state. The system uses the optimum policy to automatically disconnect or self-reconfigure vulnerable services and thus slow down the progression of the attack at any node of the system. Finally, continuous learning and scanning of vulnerabilities allows the system to adapt to new threats.
Challenges and Future Work
Modeling IoT presents several challenges that will be addressed in our future work. First, IoT devices may be autonomous and may not have a global knowledge of the network [21]. Also, directives sent from a central command to IoT devices may be delayed or lost. Therefore, a distributed security mechanism is more appropriate in IoT compared to the traditional attacker vs defender model.
Moreover, an IoT network may be subject to several simultaneous attacks from different point of the network, and at different stages of the kill chain. Those attackers may be acting independently or in collusion. The case of colluding attackers [24] is particularly challenging.
Monitoring is another key consideration. There are scenarios, where players cannot observe the other player’s actions directly but can only observe an imperfect noisy signal correlated to those actions. For instance, the defender may not know exactly the last edge-vulnerability exploited by the attacker or can only infer the new position of the attacker in the attack graph.
Furthermore, IoT devices may have a short time to process a large amount of information in a complex environment with finite memory and limited computational power. This results in the limited rationality of IoT nodes which result in incorrect decisions that deviates from rational equilibrium behavior. Prior work has used evolutionary game theory [25]-[26] and prospect theory [27] to account for limited rationality.
Machine learning entails improvement of a computer’s performance on a given task with experience. Machine learning algorithms and approaches are also important to our proposed framework for proactive cyber defense. Specifically, using 60 different classifiers (or supervised learning algorithms), Lee et al. [28] deploy honeypots and accurately identify social spammers on Twitter and MySpace. Furthermore, it is known that evolution-based algorithms that combine machine learning and genetic algorithms can advance cyber agility by periodically changing the system’s configuration and attack surface [29]-[30]. In addition, a key aspect of proactive cyber defense and cyber resilience is cyber-risk quantification—this process involves predicting the number of successful cyber-attacks [31]. Moreover, each of these components of proactive cyber defense require robust intrusion detection systems (IDS) that are behavior or anomaly-based to detect the zero-day cyber-attacks instead of the classical signature-based detection models that are found exclusively in many IDS. For example, Alazab et al. [32] demonstrated that using support vector machines, a type of supervised learning algorithm, obfuscated malware can be effectively detected. However, there is the need to fully understand the limitation and vulnerabilities of machine learning algorithm [33]. The potential manipulation of those algorithms by an intelligent adversary introduces new threats that need to be investigated. In fact, all IoT devices rely on algorithms based on artificial intelligence and machine learning to operate. Future battlefields will have IoT devices (e.g., robots, drones) from opposing armies [1]. Those IoT devices may have other IoT entities as adversaries. An easy way to win a battle will be to manipulate the algorithm from the opposing IoT. The new and fertile field of adversarial machine learning is at the intersection of game theory and machine learning is promising.
- A. Kott, A. Swami, B. West. “The internet of battle things”. IEEE Computer, Dec. 2016.
- Edward J. M. Colbert and Alexander Kott, “Cybersecurity of SCADA and Other Industrial Control Systems”, Springer International Publishing, 2016.
- Michael Hiltzik, “Apple, the FBI, and the Internet of Things: Your whole house is open to attack” Los Angeles Times, March 1, 2016, available online: http://www.latimes.com/business/hiltzik/la-fi-mh-apple-the-internet-of-things-vulnerable-to-attack-20160301-column.html [July 11, 2017]
- John R Johnson, et al., “A graph analytical metric for mitigating advanced persistent threat,” 2013 IEEE Intelligence and Security Informatics Conference,
- E. Purvine, et al., “A graph based impact metric for mitigating lateral movement cyber-attacks,” ACM Workshop on Automated Decision Making for Active Cyber Defense, 2016
- J. Vukalovic and D. Delija., “Advanced Persistent Threats, Detection and Defense” IEEE Information and Communication Technology, Electronics and Microelectronics (MICRO) 2015
- Stacey Higginbotham, “Samsung’s smart fridge could be used to steal your Gmail login” Fortune, Aug 24, 2015, available online: http://fortune.com/2015/08/24/samsungs-smart-fridge-hacked/ [July 11, 2017].
- Roger B. Myerson, “Game Theory: Analysis of Conflict” Harvard University Press, (1991).
- Gael Kamdem, Charles A. Kamhoua, Yue M. Lu, Sachin Shetty, Laurent Njilla “A Markov Game Theoretic Approach for Power Grid Security” in the proceedings of the IEEE International Conference on Distributed Computing Systems (ICDCS 2017) workshop, Atlanta, GA, June 2017.
- Charles A. Kamhoua, Kevin Kwiat, Joon Park “Surviving in Cyberspace: A Game Theoretic Approach” in the Journal of Communications, Special Issue on Future Directions in Computing and Networking, Academy Publisher, Vol. 7, No 6, June 2012.
- M. Zhao, F. D’Ugard, K. A. Kwiat and C. A. Kamhoua, “Multi-level VM replication based survivability for mission-critical cloud computing,” 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, 2015, pp. 1351-1356.
- Dave Climek, Anthony Macera, Walt Tirenin “Cyber Deception” Special Issue of Cyber Security and Information Systems Information Analysis Center (CSIAC) Journal, Focus on Air Force Research Laboratory’s Information Directorate, Volume 4, Number 1, December 2015.
- Patrick McDaniel, Ananthram Swami “The Cyber Security Collaborative Research Alliance: Unifying Detection, Agility, and Risk in Mission-Oriented Cyber Decision Making” Cyber Science & Technology at the Army Research Laboratory (ARL), Volume: 5 Number: 1, January 2017.
- Charles A. Kamhoua, Patrick Hurley, Kevin Kwiat, Joon Park “Resilient Voting Mechanisms for Mission Survivability in Cyberspace: Combining Replication and Diversity” in the International Journal of Network Security and Its Applications (IJNSA), Vol.4, No.4, July 2012.
- Karel Durkota, Viliam Lisy, Branislav Bosansk and Christopher Kiekintveld, “Approximate Solutions for Attack Graph Games with Imperfect Information, in the proceedings of the International Conference on Decision and Game Theory for Security, London, UK, November 2015.
- Hayreddin Ceker, Jun Zhuang, Shambhu Upadhyaya, La Quang Duy, Soong Boon Hee “Deception-based Game Theoretical Approach to Mitigate DoS Attacks” in the proceedings of the International Conference on Decision and Game Theory for Security, New York, November 2016.
- Q Zhu, T Basar “Game-theoretic approach to feedback-driven multi-stage moving target defense” in the proceedings of the International Conference on Decision and Game Theory for Security, Fort Worth, TX, November 2013.
- Tansu Alpcan, Tamer Basar “A game theoretic analysis of intrusion detection in access control systems” in the proceedings of the 43rd IEEE Conference on Decision and Control, 2004.
- Muhammed Sayin, Tamer Basar “Secure Sensor Design for Cyber-Physical Systems Against Advanced Persistent Threats” in the proceedings of the International Conference on Decision and Game Theory for Security, Vienna, Austria, November 2017.
- Cuong T. Do, Nguyen H. Tran, Choongseon Hong, Charles A. Kamhoua, Kevin A. Kwiat, Erik Blasch, Shaolei Ren, Niki Pissinou, Sundaraja Sitharama Iyengar “Game Theory for Cyber Security and Privacy” ACM Computing Surveys (CSUR), Volume 50, Issue 2, Article No. 30, June 2017.
- Leslie, N., Singh, R., Rigaki, M., & Yang, S. (in press). “Applying Machine Learning Algorithms to Cyber-Physical System Security Challenges”. NATO Technical Report for NATO STO IST-152 Task Group on Intelligent Autonomous Cyber Defence and Resilience. NATO.
- National Vulnerability Database, https://nvd.nist.gov/
- Common Vulnerability Scoring System, nvd.nist.gov/cvss
- Abhishek Roy, Charles A. Kamhoua, Prasant Mohapatra, “Game Theoretic Characterization of Collusive Behavior among Attackers” in the proceedings of the 2018 IEEE Conference on Computer Communications (INFOCOM), Honolulu, HI, April 2018.
- C. A. Kamhoua, N. Pissinou and K. Makki, “Game Theoretic Modeling and Evolution of Trust in Autonomous Multi-Hop Networks: Application to Network Security and Privacy,” 2011 IEEE International Conference on Communications (ICC), Kyoto, 2011, pp. 1-6.
- C. A. Kamhoua, N. Pissinou, J. Miller and S. K. Makki, “Mitigating routing misbehavior in multi-hop networks using evolutionary game theory,” 2010 IEEE Globecom Workshops, Miami, FL, 2010, pp. 1957-1962.
- W. Saad; A. Sanjab; Y. Wang; C. Kamhoua; K. Kwiat, “Hardware Trojan Detection Game: A Prospect-Theoretic Approach,” in IEEE Transactions on Vehicular Technology , vol.PP, no.99, pp.1-1.
- Lee K, Caverlee J, Webb S. Uncovering social spammers: social honeypots+ machine learning. InProceedings of the 33rd international ACM SIGIR conference on Research and development in information retrieval 2010 Jul 19 (pp. 435-442). ACM.
- John DJ, Smith RW, Turkett WH, Cañas DA, Fulp EW. Evolutionary based moving target cyber defense. InProceedings of the Companion Publication of the 2014 Annual Conference on Genetic and Evolutionary Computation 2014 Jul 12 (pp. 1261-1268). ACM.
- Zhuang R, DeLoach SA, Ou X. Towards a theory of moving target defense. In Proceedings of the First ACM Workshop on Moving Target Defense 2014 Nov 7 (pp. 31-40). ACM.
- Leslie, N., Harang, R. E., Knachel, L. P., & Kott, A. (2017). “Statistical models for the number of successful cyber intrusions”. The Journal of Defense Modeling and Simulation, 1548512917715342.
- Alazab, M., Layton, R., Venkataraman, S. and Watters, P., 2010. Malware detection based on structural and behavioural features of API calls.
- N. Papernot, P. McDaniel, S. Jha, M. Fredrikson, Z. Celik, and A. Swami. The limitations of deep learning in adversarial settings. Proceedings of the IEEE European Symposium on Security & Privacy, 2016.


