On September 14, 2010, then Under Secretary of Defense for Acquisition, Technology and Logistics (USD(AT&L)), Dr. Ashton Carter, provided guidance to acquisition professionals regarding the “Better Buying Power” initiative. The Department of Defense (DoD) introduced Better Buying Power – with broad support from senior DoD leadership – to improve acquisition value through increased competition, tradecraft, productivity and incentives. Better Buying Power also focused heavily on how the Department managed its complex acquisition portfolio by challenging the workforce to improve critical acquisition management, oversight and processes. The Department would achieve better acquisition management and processes, according to Better Buying Power, with a greater focus on cost, affordability and performance – elements that were becoming increasingly important as DoD faced growing scrutiny on its acquisition programs.
The timing of Better Buying Power was no surprise. In 2010 the Department’s Major Defense Acquisition Program (MDAP) portfolio grew to over $1.7 trillion across the life of the programs, an almost 60% increase from acquisition numbers reported ten years earlier. The $1.7 trillion did not account for certain operations and sustainment costs, the Military Department’s smaller acquisition programs, or Major Automated Information Systems, adding billions to an already incredible portfolio. DoD’s acquisition processes were also the subject of ongoing Congressional scrutiny and numerous Government Accountability Office (GAO) and DoD Inspector General (IG) investigations. Highlighting significant management and oversight issues, the GAO claimed that development costs for acquisition programs were as much as 42% higher than original estimates, with program delays averaging 22 months. While DoD worked closely with GAO to review their conclusions, the scope of the portfolio is real.
Better Buying Power provided a strategic foundation to implement change, but acquisition leadership still needed to answer a tough but appropriate question: did DoD have the right information or systematic processes to address acquisition management, oversight and process complexities and achieve efficiencies that provided better value to the Warfighters and taxpayers? In the September 14, 2010, Better Buying Power guidance memorandum to acquisition professionals, Dr. Carter emphasized the use of data to answer this question.
“We have analyzed data on the Department’s practices, expenditures, and outcomes and examined various options for changing our practices. We have sought to base the specific actions I am directing today on the best data the Department has available to it. In some cases, however, this data is very limited. In these cases, the guidance makes provision for future adjustments as experience and data accumulate so that unintended consequences can be detected and mitigated.”
The message was clear: data and information were key to managing, overseeing and streamlining processes within the acquisition portfolio, but DoD would require diligence to obtain it. Data offered innovative perspectives on acquisition processes, delivering the necessary insight into acquisition cost, performance, affordability and other critical elements. Empowered with data, DoD leadership could report, analyze, and make informed decisions on the Department’s complex acquisition portfolio. This is the focus of this article.
Prior to Better Buying Power, the Director of Acquisition, Resources and Analysis (ARA), an organization under the USD(AT&L), led a parallel effort to support the reformation of acquisition management, oversight and departmental business processes. The Director, ARA directed a small team to focus on using structured data to provide insight on how the Department viewed and managed its acquisition portfolio. Key areas of focus were data governance and using data as a service. In conjunction with the Military Departments, the team demonstrated it could identify authoritative sources of major acquisition information; have consistent, semantic definitions across the Department; measure data for accuracy, reliability and availability; and provide it to acquisition leadership for use in any visual tool giving them data-driven insight into the major acquisition portfolio.
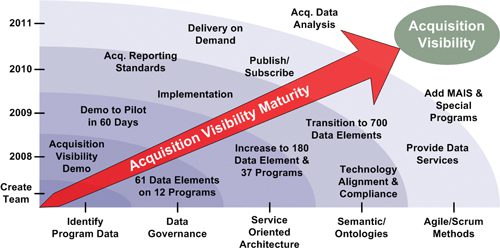
These efforts were part of a pilot that went from concept to execution in under 60 days – a short order for a complex Department of Defense. The team extracted performance data elements of 12 major weapons programs and presented this data to leadership within a service-oriented environment. DoD leadership would manage this service Department-wide with the goal of supporting reporting, analysis and decision making. Although the pilot represented a small subset of acquisition data and programs, it demonstrated two important achievements: first, DoD could manage and govern acquisition information with technologies and techniques such as Service Oriented Architecture (SOA) and semantics; second, DoD could provide data and information as a service in a near real-time environment. The ability for this team to reach across DoD and work closely with the Military Departments showed transcendence of organizational boundaries, infrastructures, organizational prerogatives, and security models. Acquisition data – once held tightly by those processes – was now transparent and understood. The USD(AT&L) saw the potential structured data could have on acquisition management, oversight and business processes and expanded the pilot to determine its full capability. Additionally, he sought an on-demand environment that could provide data across the enterprise seamlessly and efficiently. This capability became known as Acquisition Visibility (AV), which transitioned from pilot to implementation, formally effective in July 2009. The number of acquisition programs covered under Acquisition Visibility tripled during this transition and the team worked across the Department to apply structured acquisition data to other uses. They began to automate reporting to immediately comply with internal and Congressional reporting requirements and reused data to develop multiple reports at the same time. In support of other organizations, including the Office of Performance Assessments and Root Cause Analyses, DoD began to explore the use of data analytics, using business intelligence tools to provide dramatically better insight to leadership about how DoD oversaw and managed its acquisition programs. This also provided leadership awareness into how DoD’s industry partners were performing against their requirements and obligations. As data requirements increased, Acquisition Visibility quickly became the single source for acquisition information across the Department.
An Effective Capability Through Agility
While Acquisition Visibility provides important information to acquisition decision-makers, it is more than a technical capability which shares information across the Department. The service is the authoritative source for acquisition information, acquisition information definition and the foundation for how acquisition leadership oversees, manages, reports and analyzes its major acquisition portfolio. It delivers the core service for the USD(AT&L)’s acquisition oversight, accountability and strategic decision making. Acquisition Visibility leverages internal net-centric services from OSD defense agencies as well as engineering and technical expertise from the Military Departments and industry partners. Components now provide accurate, structured, acquisition information – via AV SOA as the core element of net-centricity – immediately to the USD(AT&L) and senior decision makers.
Acquisition Visibility does not impose uniform business processes across the DoD acquisition community, replace current applications and tools or implement an “IT solution”. It benefits from best practices, SOA and existing technical infrastructure to gain access to transparent, acquisition data without having to maintain a single data strategy or common infrastructure – each Component optimizes their business processes and leverages technologies as appropriate. Data governance ensures access to Component-managed acquisition information and defines data for consistency, accuracy and reliability across the Department. Governance also establishes definitive semantic meaning to the business rules so Components share acquisition information consistently within the AV environment. This enables Components, leadership and acquisition stakeholders to view and measure data uniformly and promotes information quality assurance when it comes to data reporting and analysis.
Multiple delivery teams support Acquisition Visibility providing functional, technical and data expertise. Acquisition Visibility now covers all major defense acquisition programs, by sharing sustainment, operating costs and earned value management data among other acquisition information. AV leadership has transitioned the service into a production environment and grew the number of acquisition data elements to over 700 bringing additional, more relevant information to acquisition decision makers. The Department will add the Major Automated Information Systems and non-MDAP acquisition programs to this information paradigm in the near future. Figure 1 below provides a visual of Acquisition Visibility and its core services. In support of Acquisition decision making, DAES, SAR, UCR, DAB and APB are legislative reporting requirements or decisions forums that leverage acquisition information via Acquisition Visibility.
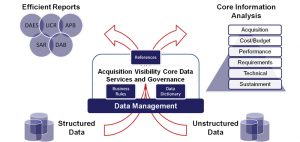
Figure 1: Strategic View of the Acquisition Visibility service